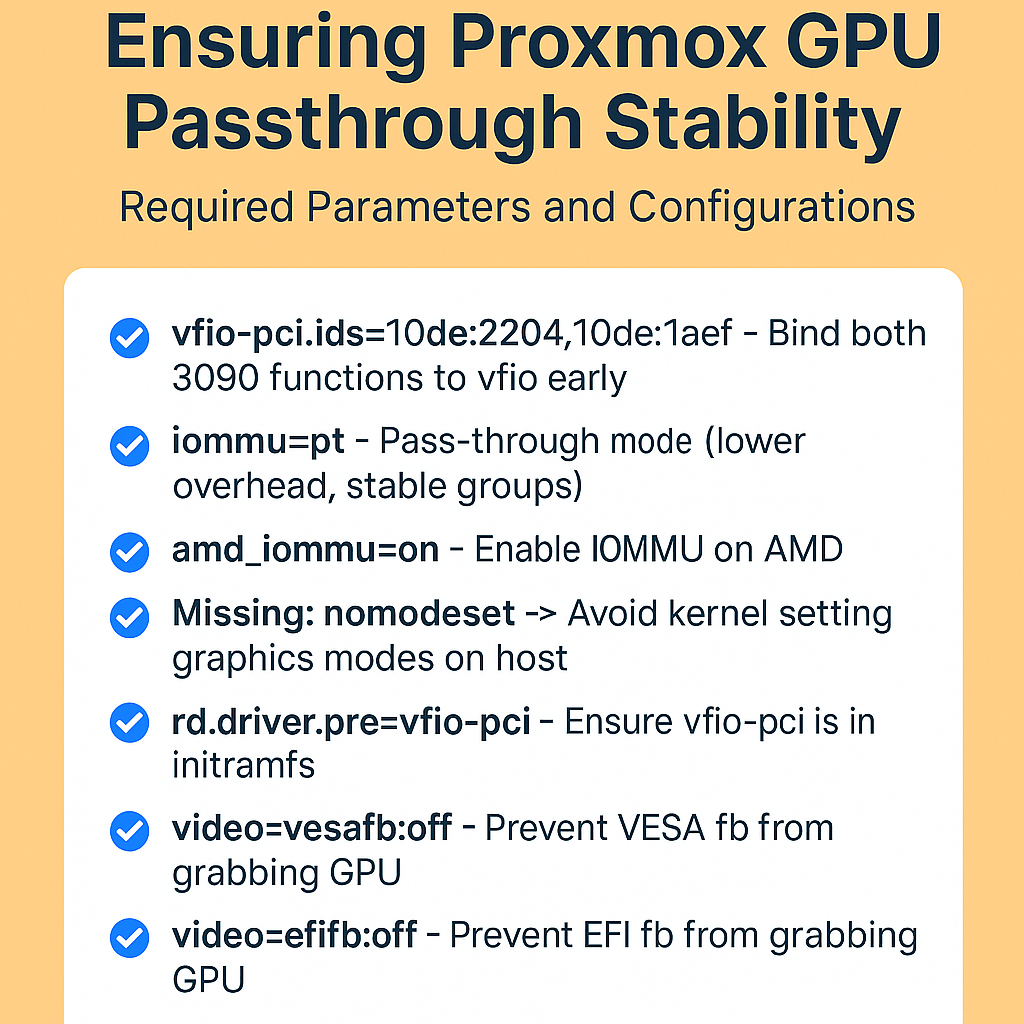
As part of my multi-cloud research, I wanted to test Oracle Database Service for Azure. In this article, you will see how to sign up for the new service and how to link Oracle and Azure accounts. I used Frankfurt datacenters, Azure MSDN, and OCI paid account (Free Tier does not work) using my private Azure Active Directory.
First and foremost my biggest learning from testing Oracle Database Service for Azure is this: you need to have a paid OCI account, it will not work with the Free Tier offering.


The next thing is to think and design a little before you start clicking on the cloud portals. Azure and Oracle Cloud-link is a networking-heavy exercise, you have to be keen on what you enter into the networking dialogue to deploy this right. Automation will help you to connect clouds behind the scenes, but only if you provide the proper networking details.














In my next article, I will share my ideas of how to connect Azure services to the newly provisioned OCI database utilizing automatically provisioned and free-to-use OCI-Azure cloud-link.

By the time I am writing this article, everything worked for me what I wanted to test, stay tuned, I will continue to share my learnings on Azure Oracle Services / Oracle Database Service for Azure.